Container Security Best Practices
General security best practices to secure containers in your environments.
Developing with Python in Regulated Environments (FedRAMP Edition)
A FedRAMP focused guide when developing in Python
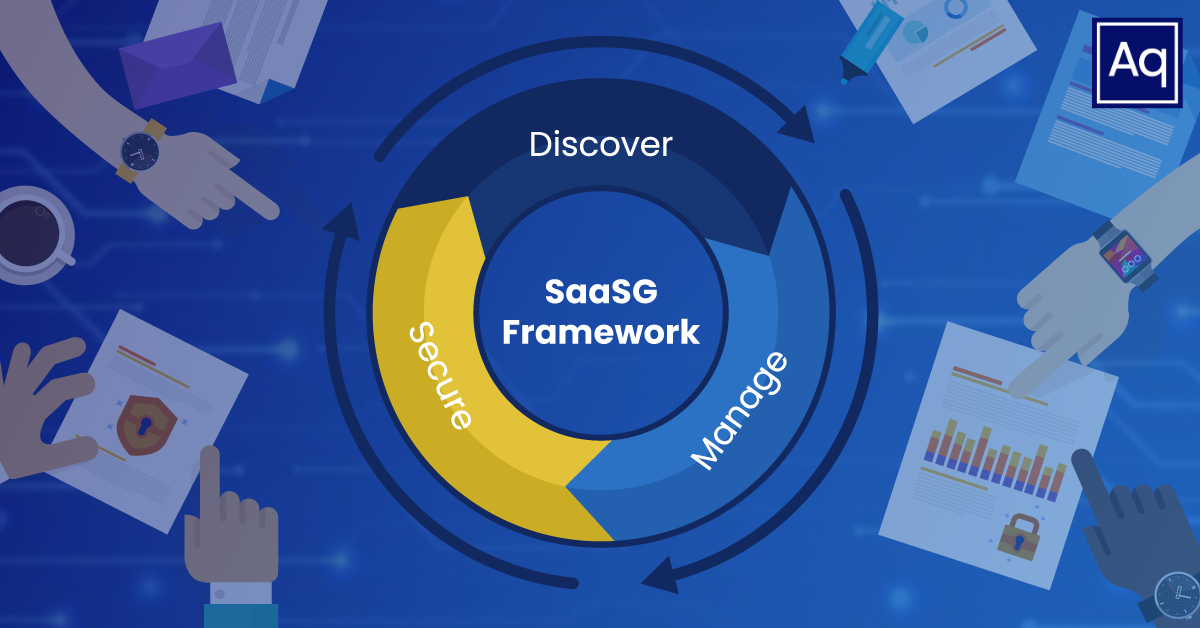
❄️ Snowflake Safe. The Importance of SaaS Governance
Effective SaaS Governance. A view into how Snowflake can remain safe.
Don't get stung!🐝 A Peek Into Emerging Risks In AI Technologies and Organizational Strategies For Mitigation.
A snapshot into various risks posed by modern AI technologies
Breaking Down the NSA’s Guidance on Zero Trust Implementations for the Applications and Workloads Pillar
A look at how the NSA’s guidance aims to simplify incorporating Zero Trust principles into enterprise networks
When Zero Trust Makes Zero Sense
Exploring what this buzzword means and how it can lay the foundation for a more effective security practice when approached correctly
Top 5 Reasons CMS's SEAS IT AI Contract Is One to Watch
The CMS SEAS IT AI contract is a forward-thinking blueprint for the future of government healthcare systems. Learn more about the top five reasons why it's a contract to watch.
Do you have Container Base Image CVEs? Switch to Alpine Linux to reduce CVEs!
Switch to Alpine Linux to reduce CVEs!
Uncle Sam Wants YOU (To Learn To Code) – And He’s Got An Apprenticeship Program For It
How apprenticeships can help us close the cyber employment gap and help us win the cyber war
Key Updates in FedRAMP Governance and Regulations
Learn more about changes driven by an updated FedRAMP roadmap, RFQ for a GRC solution, and pen testing guidance for public comment.
The New NIST SP 800-171 Revision 3 is Here! Comparing Revisions 2 and 3
After nearly two years of waiting, NIST SP 800-171 Revision 3 is final. Here are the major changes to consider.
10 Essential Questions to Ask When Outsourcing FedRAMP Continuous Monitoring (ConMon)
Unlock the key to selecting the right service provider for your FedRAMP ConMon needs. Explore the 10 essential questions to ask, empowering you to evaluate effectiveness and ensure compliance.
Navigating The New FedRAMP Board and Federal Secure Cloud Advisory Committee (FSCAC) Changes
FedRAMP Governing Body Making Major Changes
Successfully Transitioning from Project to Product Delivery: Five Key Strategies
How and why product-based paradigms drive valuable outcomes for organizations.
Can Collaboration with Enterprise Tech Solve the Federal Zero Trust Problem
A Fresh Federal Perspective at Axonius Adapt and How it Impacts Zero Trust Security
Recap of the 2024 Cloud Compliance Summit
Aquia and AWS hosted the 2024 Cloud Compliance Summit on March 19. Looking for an overview of the topics discussed? We've got you covered!
How I Passed the New CSA Certificate of Competence in Zero Trust (CCZT) Exam, and Why You Should Take It Too
Breaking down CSA’s new CCZT exam, and it’s utility as a resource for GRC practitioners and technical security operators looking to learn more about Zero Trust
Insights into DoD's New FedRAMP Moderate Equivalency Guidelines for Cloud Providers
Navigating the FedRAMP Equivalency Memo and DoD Regulations
Exploring the GitHub Advisory Database for fun and (no) profit
Principal Security Engineer Dakota Riley dives into the GitHub Advisory Database, cross referencing with other data sources and looking for interesting trends
Has Your SaaS Gotten Sassy? Know When Your SaaS-to-SaaS Interconnections Have Gotten Too Loquacious.
Know when SaaS-to-SaaS crosstalk has crossed the line.
Who Dropped the SBOM 💣? How to Size-Up Tooling in an Inchoate Space.
16 things to look for when evaluating SBOM tooling.
The Importance of Threat Modeling for Building Secure Workloads in AWS
Assessing the impact and process of threat modeling workloads in AWS
Wait, I Needed That: Criticality Analysis
Exploring the important role of a criticality analysis in evolving the security posture of organizations, from a traditional and zero trust-focused perspective.
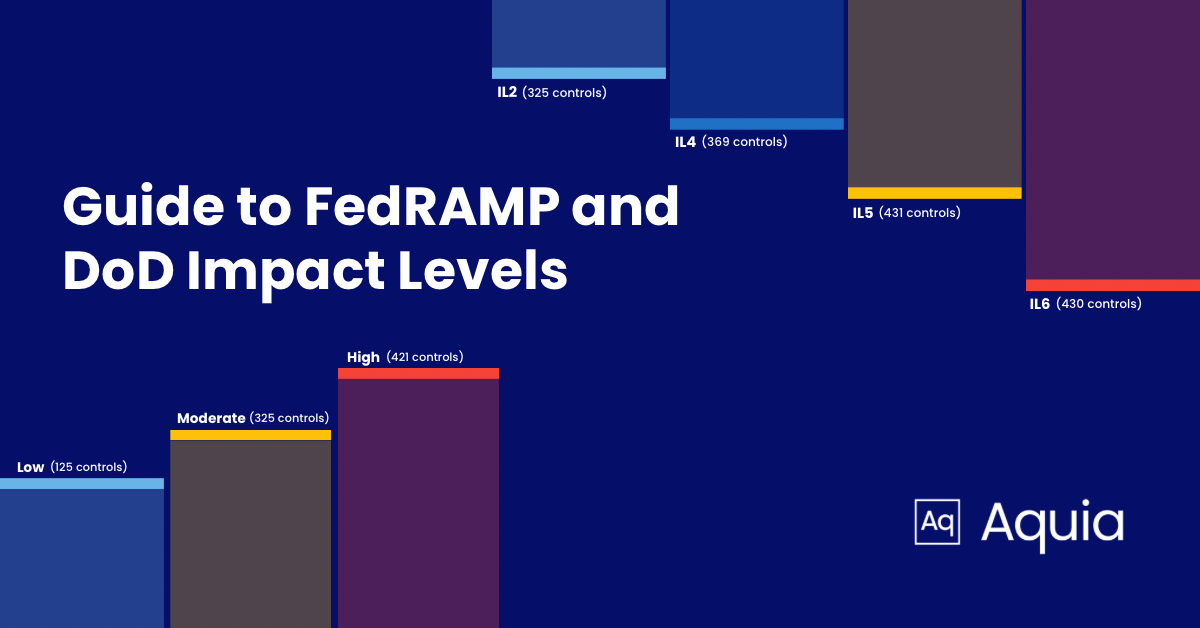
A Guide to FedRAMP Levels and DoD Impact Levels for CSPs
Understanding the FedRAMP Authorization & DoD Impact Levels, and how they align
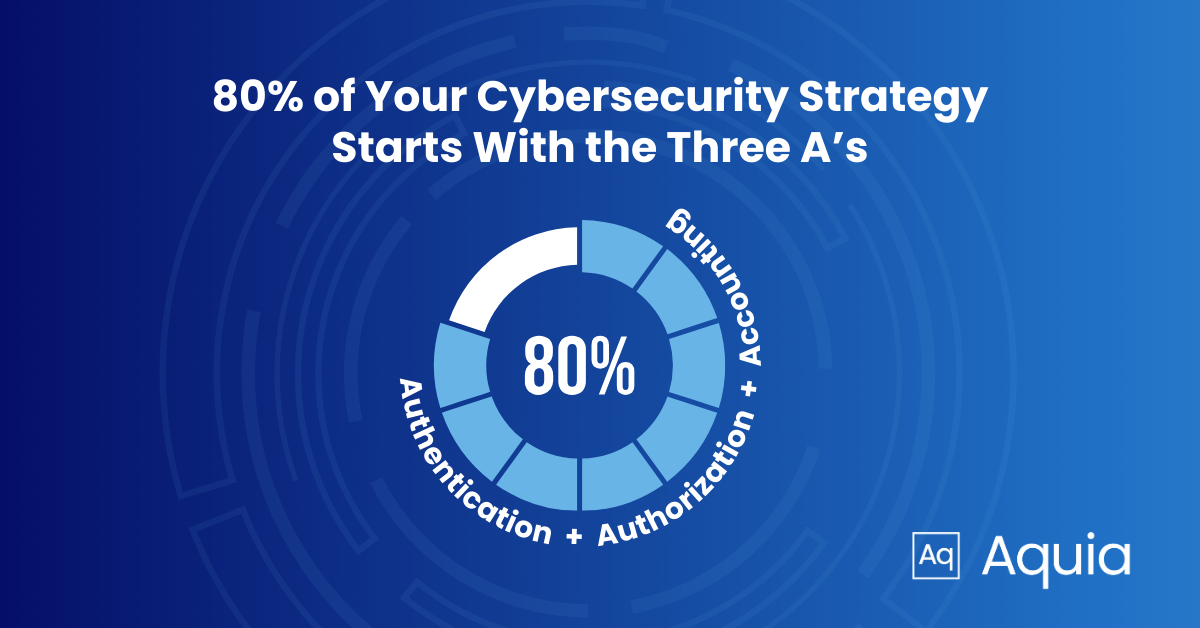
Cybersecurity Meets Pareto - The Three A's (AAA)
Authentication, Authorization, and Accounting
Secure Self-Hosted Runners for GitHub Actions Leveraging Amazon ECS
A review of security concerns relating to runners for GitHub Actions, and how you can securely manage your own self-hosted runners on Amazon ECS with Fargate.
I Sat for the CISSP Exam. I Passed. Here's How.
Steps I took to prepare for the CISSP exam.
The Top 4 SaaS Security Challenges and How To Overcome Them
Navigating the pitfalls of visibility, permissions, responsibility, and emerging threats.
AWS ReInvent and PreInvent security recap
A recap of the releases from around Re:Invent!
Understanding the Importance of Gap Assessments as a Governance, Risk, and Compliance Apprentice
Gap Assessments - Applicable to systems, and personal growth!
Soft Skills in Cybersecurity: Breaking the Imposter Syndrome Code and Bridging the Entry-Level Gap
Challenges to breaking into cybersecurity, and how one career-pivoter overcame them
Driving Actionable Work From a Threat Model
A recap of the talk-turned-workshop I presented at the inaugural Threat Modeling Convention (ThreatModCon).
Breaking Down the Modernizing FedRAMP Memo
Aquia President Chris Hughes in this article breaks down the recently published Modernizing FedRAMP Memo from the Office of Manangement and Budget (OMB) and discusses key implications for the future of FedRAMP and its impact on the Federal and commercial cloud markets
From Apprentice to Advocate - My Journey at Uniting Women in Cyber Conference
Aquia GRC Apprentice Elif Sumner writes about her experience attending the Women in Cyber (WiCyS) conference
Cybersecurity...How Did I Get Here and Why Are There So Many Acronyms?
Breaking into cybersecurity as a career-pivoting woman with a non-technical background
Announcing the Amazon GuardDuty Runbook Generator
An open-source tool to kickstart runbook creation
The Importance of FedRAMP Authorization for Cloud Service Providers
Why a CSP should make a significant investment into FedRAMP authorization
Aquia Open Source Contributions - Adding a CISA KEV Enrichment Table to Matano
Principal Security Engineer Dakota Riley writes about contributing CISA KEV Enrichment Tables to Matano
How to Sign Container Images Using Cosign
A demo of signing a container image using Cosign with a Cosign locally generated key and an AWS KMS key.
Signing Software Artifacts With Cosign
Learn about the importance of signing software artifacts using Cosign to help secure the software supply chain.
SaaS Governance - A Critical Industry Need
A critical industry need that shows no signs of slowing down!
Resiliency, Cyber Risk, and Injury Prevention
There are many challenges in data-driven risk reduction. Sports Injury Prevention offers an apt analogy for discussing the mindsets involved in building resilient architectures.
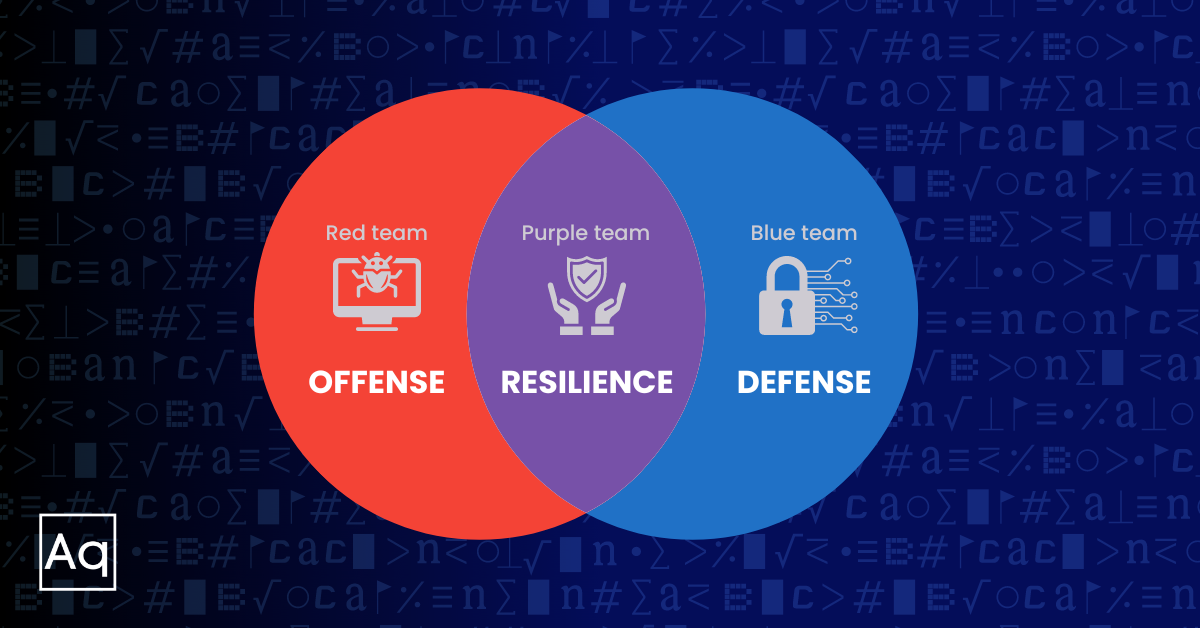
“So, You’re Building a Purple Team?”
Having built and scaled Purple Team programs at every organizational level, we can tell you that no two are the same. Before you start your own, check out our tips for ensuring your team’s success.
The Benefits Of Using SaaS Security Posture Management (SSPM)
Exploring what SSPM is and the benefits of leveraging it in your security stack
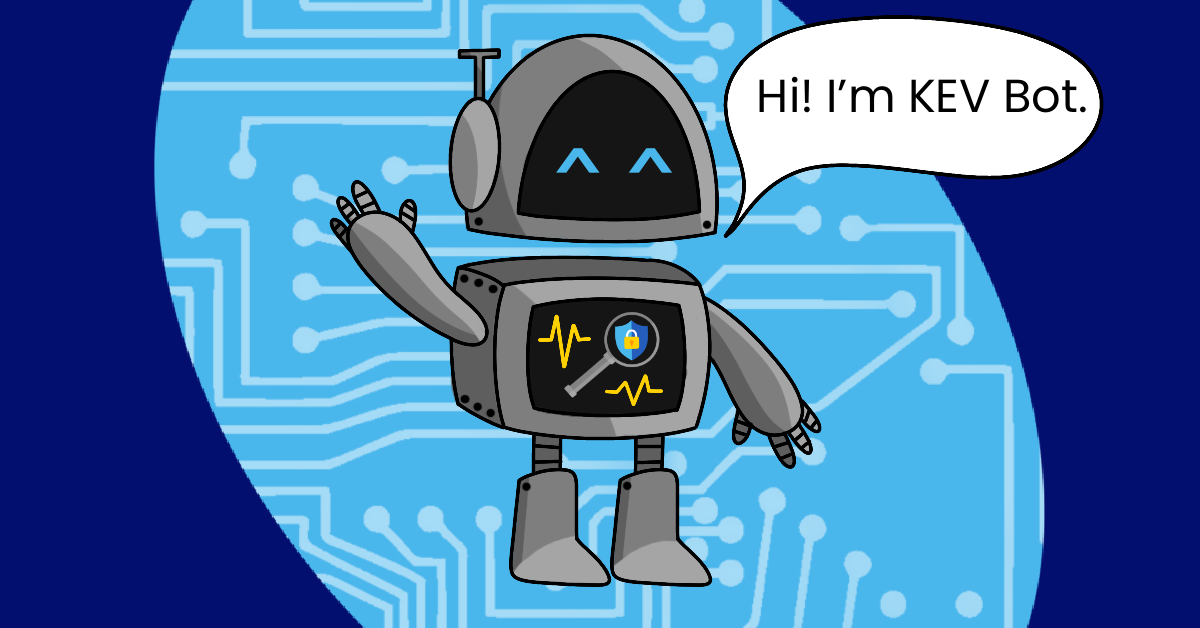
Introducing KEV Bot, Our Known Exploited Vulnerabilities Bot
An introduction to Aquia's KEV notification system
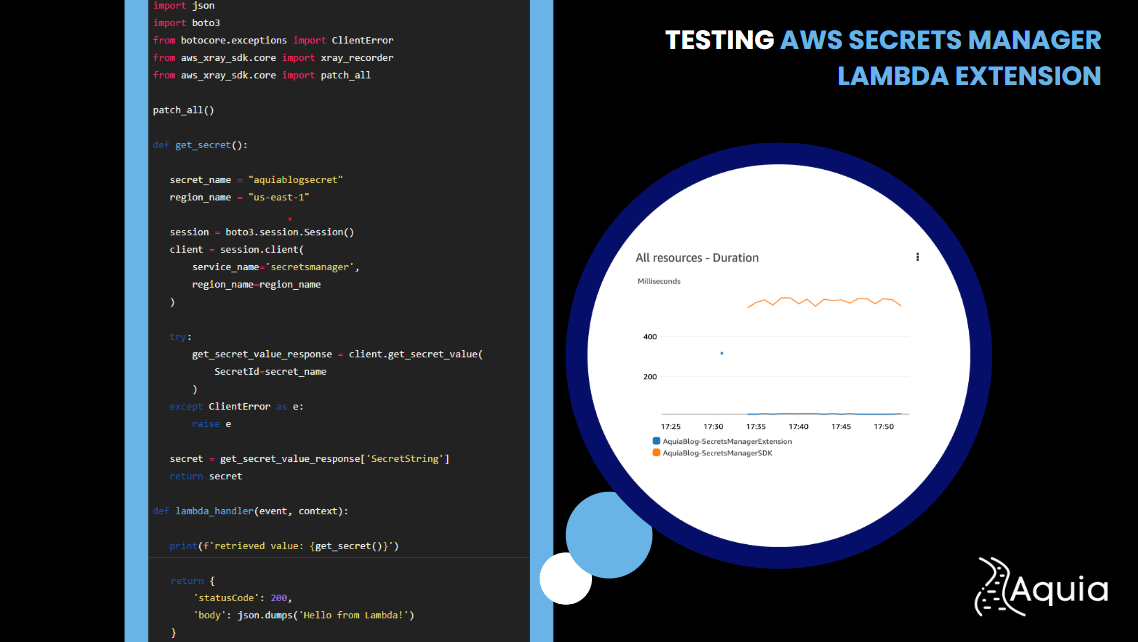
Taking The New Secrets Manager Lambda Extension For a Spin
Walkthrough on using the new Lambda Extension to retrieve secrets, and comparison against using Boto3
The Importance of Internal Cloud Security Standards
Why an internal cloud security standard is important and how to create one
AWS Re:Invent 2022 Security Recap and Top 5 Releases
We collected the security relevant AWS releases and announcements from this years reinvent!
Exploit Prediction Scoring System (EPSS)
A look at the Exploit Prediction Scoring System (EPSS) for vulnerability management
OWASP Software Component Verification Standard (SCVS)
A look at some of the fundamental controls for each of the SCVS levels
Book Club: Cloud Native DevOps with Kubernetes
Five Meaningful Takeaways I hope you find useful from Cloud Native DevOps with Kubernetes by John Arundel and Justin Domingus
An Incomplete Look at Vulnerability Databases & Scoring Methodologies
A look at some of the fundamental vulnerability databases and scoring methodologies currently in use in the industry
How I Passed the AWS Certified Security - Specialty Exam
Tips and recommended materials used to pass the exam.
Threat Detection on EKS – Comparing Falco and GuardDuty For EKS Protection
A comparison of Falco and GuardDuty for EKS Protection.
Psychological Safety: Easier Said than Done
Knowing is only the first step. Doing takes practice.
Psychological Safety
Learn about psychological safety, its importance, and how to foster it in your teams.
Auto Remediation with Eventbridge, Step Functions, and the AWS SDK Integration
Learn how to use the AWS SDK for Step Functions to auto-remediate findings.
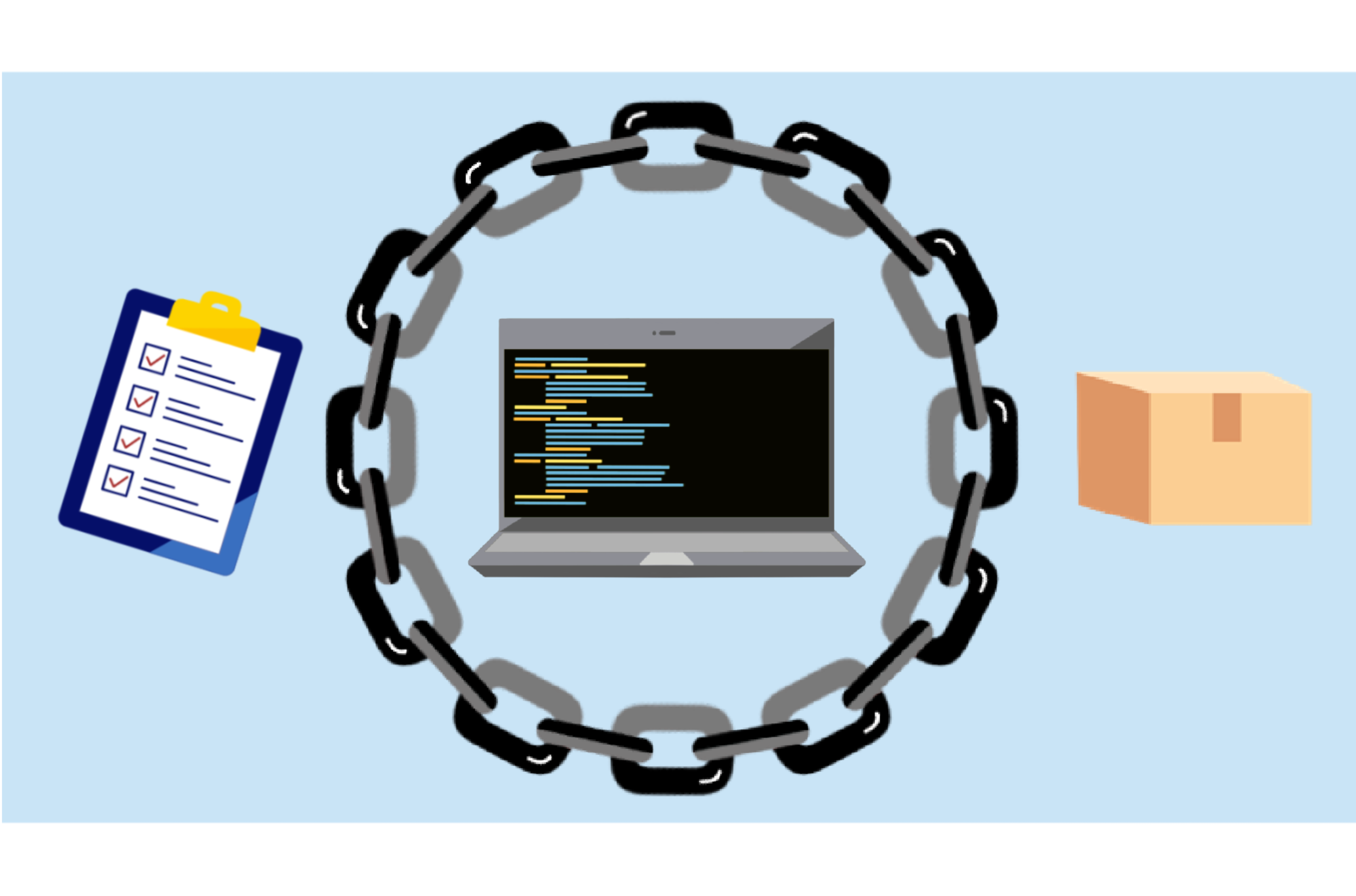
Supply Chain Risk Management
Supply chain security is rapidly becoming a top concern of most technology and security leaders. This article will examine some of the background, relevant efforts, incidents and best practices around securing the software supply chain.
Using Semgrep to find security issues and misconfigurations in AWS Cloud Development Kit projects
Learn how to find security issues and misconfigurations in AWS Cloud Development Kit projects with Semgrep.