How I Passed the New CSA Certificate of Competence in Zero Trust (CCZT) Exam, and Why You Should Take It Too
Breaking down CSA’s new CCZT exam, and it’s utility as a resource for GRC practitioners and technical security operators looking to learn more about Zero Trust

As a security architect at Aquia, I work on a Zero Trust (ZT) team identifying and architecting security solutions to support increasing Zero Trust maturity for our clients. As such, I was thrilled when the Cloud Security Alliance (CSA) rolled out their new Certificate of Competence in Zero Trust (CCZT) at the end of 2023, as there aren’t a ton of ZT-specific certs out there. I’ve run gap analyses; I’ve worked on privilege access management (PAM), phishing-resistant multi-factor authentication (PR-MFA) and micro-segmentation; this was right up my alley — right? So I sat for the CCZT without much prep, full of confidence.
And then it hit: FAILURE. I came up three questions shy of passing. Tragic. But, after some encouragement and support from my colleagues at Aquia, some renewed confidence, and a new sense of accountability to my team, I hit the learning documents hard, built a strategy, and passed the CCZT with 90% accuracy on my next try, three days later. I’ll tell you how I did it, and some unexpected things I learned about this new exam along the way.*
Hidden Value? The CCZT as Cybersecurity Context-Creator
Conceptually, I think the CSA CCZT is a great certification and learning path. As a Zero Trust Architect, I work with more technical architectures and implementations, but I got my start in the more conceptual space of governance, risk, and compliance (GRC). That background works well for me because Zero Trust in general has a foot in both the technical and conceptual camps. I often find in my daily responsibilities that there is a big comprehension gap between these two worlds, and the CCZT learning path explores fundamentals from the sometimes confusing world of granular technical implementations, and the often confounding realm of compliance legalese and conceptual guidance; providing some middle ground, context, and a common language for folks, regardless of if they have an engineering or compliance background. The CCZT can act as a primer for both compliance and engineering folks.
Here’s the Catch
The CCZT exam covers some general compliance/risk assessment/governance concepts, as well as software defined perimeters (SDP) and some pretty specific ZT architecture practices, without diving too deep into either. That said, while the goal of finding common ground between GRC and engineering through ZT is a lovely concept, the workflows, processes, and exam questions tested by the CCZT are very specific to what CSA defines as Zero Trust best practice.
Over the last year, I’ve been involved in the planning, building, and updating of Zero Trust implementations based on CISA, NIST, and DoD guidelines, but I failed my first attempt because I made too many assumptions based on general knowledge. The CCZT is pretty focused on specific CSA interpretations of “how to do Zero Trust”. That said, with their paid learning bundle, CSA gives you all that information broken down into four distinct modules (Intro to SDP, Intro to Zero Trust, Zero Trust Planning, and Zero Trust Implementation) and lets you consult that information during the test — that’s right guys, gals, and non-binary pals, like all CSA certs, it is open book!
How to Pass This Exam (Practical Insights)
Here are my “hot takes” for passing the CCZT:
-
Pay the $175 for CSA’S Zero Trust Training (ZTT) training. This is a great deal on some pretty extensive documentation that explores a comprehensive approach (planning, implementation, strategy, etc.) to Zero Trust that has serious utility past your exam, and with these documents you’re 90% of the way to passing the CCZT. While some might be tempted to forgo the paid CSA provided materials, they really do hold all the information needed to answer the questions on the CCZT and they’re searchable! You can have all the PDF modules up, and with multiple displays it becomes easier to search for keywords! Not many certification organizations allow this, so take advantage!
-
Liberal usage of the “save and return to this later” function is crucial to maximizing the 90 minutes for this exam. This feature is very user friendly on this non-proctored test, so pick up the easy wins early, “save and return to this” for harder questions, and jump around between reference docs near the end.
-
I would suggest screen grabbing (ctrl+shift+4 on Mac, Windows logo key+shift+s on PC) the SDP and Zero Trust Architecture (ZTA) diagrams for easy reference during your exam. Each of the four modules has specific diagrams that outline different angles of both these processes, and you have to refer to them regularly. I spent a lot of time hunting for the ones I needed over and over again during my test, and I wish I had thought to do this sooner.
A little good prep will take you a long way to passing the CCZT!
Keeping It High Level
Now let’s address some of the high-level concepts of Zero Trust, that help orient both GRC and more technical folks around how to implement this security framework, and set them up for success with the CCZT.
(Disclaimer: These are basic fundamentals of Zero Trust and not specific to the CSA CCZT exam. I’m not giving you any specific answers here!)
What are the foundations of Zero Trust?
-
No user or device is trusted whether they are internal or external, regardless of if they’ve been trusted before. (It’s in the name … Zero Trust y’all.)
-
Assume breach*. If they want to get in, they can, so build and maintain your system as if a breach will, or has already, happened.
-
When in doubt, micro-segment. Shrinking your attack surface and reducing blast radius is all about ensuring that data assets are separated from each other with their own distinct authentication and authorization gateways. That way, when a breach happens, very little lateral movement or privilege escalation is possible.
-
Never trust, always verify. This applies to users and services. Challenges to authentication and authorization should occur at every access point, and be revalidated regularly throughout a session.
-
Constantly monitor. User activity and heuristics, network traffic, and data health should be monitored constantly.
-
Aggregate and centralize logs for DAAS (Data, Applications, Assets, and Services). Apply real-time analytics, informing expedient access decisions and incident response (and facilitating more accurate and comprehensive investigations into incidents).
While these general ZT concepts might not give you any specific answers on the CCZT, they will keep you from wandering around cluelessly while you try to hunt down the more specific CSA interpretations of these tenants. Next up, some of the areas of the specific CSA CCZT Training to pay particular attention to.
Something For Our Excel Spreadsheet Folks
Spend time familiarizing yourself with CSA’s prescribed steps for planning and implementing ZTA, each of which has their own training module. The CCZT exam asks a lot of questions centered around the different stages of planning (“after you’ve identified XYZ for your organization, what is the next step …”) and CSA has made these workflows into their proprietary material. Knowing “how to do ZT” or “How to do a Gap Analysis” isn’t as helpful here as knowing how CSA WANTS you to do those things, so make a particular note of those processes.
This is also an incredibly useful area for our GRC folks who spend a lot of time interacting with compliance frameworks (think FedRAMP, GDPR, CMMC, ISO 27001) and risk assessments or business impact analyses (BIAs). The codified step-by-step approach that CSA lays out for both planning and implementing ZTA best practices ties these steps with enriched compliance, streamlined efficiency, and risk reduction, all of which will feel familiar.
The same applies to CSA’s treatment of Zero Trust maturity levels. There are several charts and graphics that outline the specific characteristics of all five Zero Trust pillars (identity, device, network, application workload, and data) and their respective maturities (traditional, optimal, advanced)*. It’s worth saving them as images locally, so they can be easily referenced for exact answers. Similar to how some of the first steps in a threat model or a compliance assessment are to define the criticality of organizational resources, and the risk-appetite of its stakeholder groups, these maturity levels, and their mapping to the security capability pillars, represent a sliding scale of maturity that anyone familiar with GRC should be confident in.
* Note: there is no “initial” maturity like we are used to seeing in the CISA Zero Trust maturity model (ZTMM), so make sure you are familiar with CSA’s flavor of what these maturity levels are.
And Something for the CLI > UI Set
OK hoodie-wearers, if that last section made your eyes glaze over, this next part is for you: Surprise, there’s some real networking content tested on the CCZT! Most significantly, the SDP, and how its workflow enables and enhances Zero Trust maturity.
SDP is a security framework that assumes no implicit trust within a network, requiring verification from everyone and everything trying to connect. This approach:
- Reduces the attack surface
- Minimizes the risk of unauthorized access
- Enhances system efficiency
Let’s be clear: What SDP is, and your comprehension of how it works, is tested heavily here (approaching 50% of the exam — you get an entire study module for it). So, let’s quickly go over the basics:
Software Defined Perimeter (SDP) consists of several key network components that work together to create a secure and flexible network access framework. The CCZT test focuses on how SDP can help mitigate issues created by CSA’s “Egregious 11” and the OWASP “Top 10” (clearly outlined in docs). From a high level, the networking components of the SDP are;
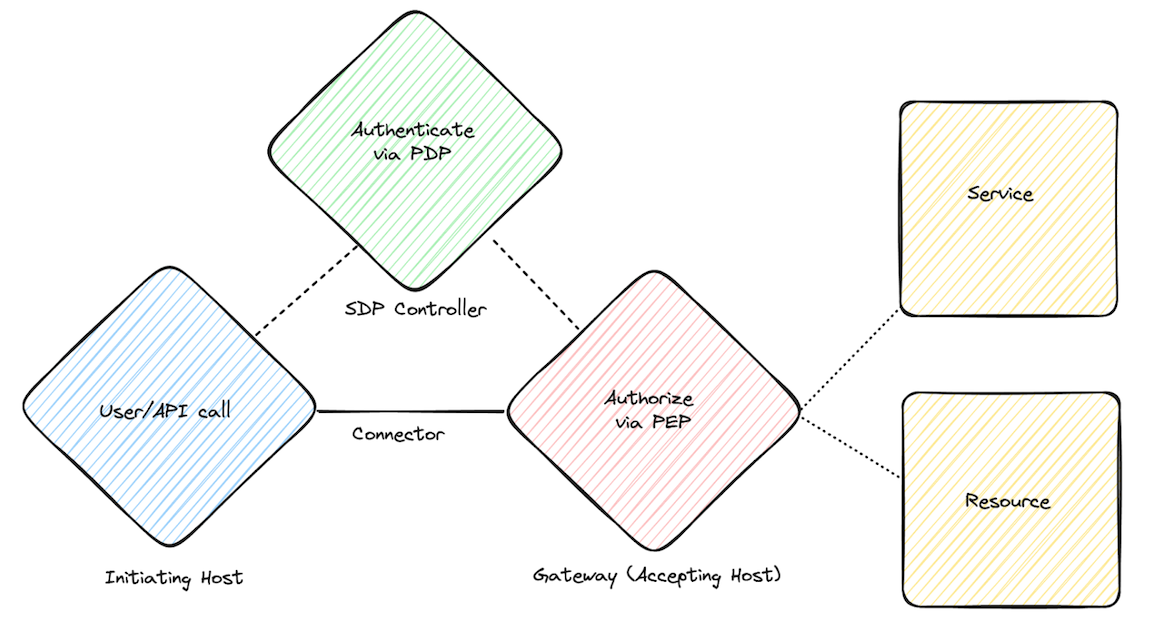
Initiating Host: Initiating hosts (IH) are endpoint devices like laptops, tablets, and smartphones running software that connects them to a secure access service edge (SASE) platform. The software on these devices helps them securely connect to the platform, allowing them to authenticate and access resources after going through a verification process. While an IH is only onboarded into the SDP once, the user or API calls initiated through the IH are authenticated and authorized each time a communication request is made.
Connector: Connectors are lightweight software components installed on user devices or within the infrastructure. They facilitate secure communication between the user’s device and the SDP gateway.
Controller: This is the central management component that orchestrates the entire system. The policy engine within the controller defines the access policies, maintained by the policy administrator, and determines who can access what, based on various factors such as user roles, device attributes, location, and security posture. These policies, set and maintained by the policy administrator, enforce who can access what. The general Zero Trust concept of the policy decision point (PDP) exists within the SDP controller.
Gateway (Accepting Host): SDP gateways act as intermediaries between users/devices and the resources they want to access. They are responsible for enforcing the access policies set by the controller. Gateways verify the user’s identity and device integrity before granting access to specific applications or services. The Zero Trust concept of the policy enforcement point (PEP) exists in the SDP gateway, and, based on the decision made by the SDP controller or PDP, either grants or denies users or APIs access to services and resources. SDP gateways/accepting hosts are only visible to authorized IHs.
In the workflow, when a user or device attempts to access a resource, the SDP system follows these steps:
The user or device making requests via the IH is authenticated using multiple factors, such as username/password, multi-factor authentication, device certificates, or other contextual information (ABAC). The controller evaluates the access request against the predefined policies. If the user and device meet the criteria, the controller generates a unique cryptographic identifier, authorizing the request. The connector on the user’s device and the SDP gateway use the cryptographic identifier to establish a secure, isolated connection to the requested services or resources.
Final Thoughts
The CCZT is a useful practice to help security practitioners of all kinds increase their contextual understanding of core Zero Trust principles and architecture, and how it comprehensively impacts both technical and non-technical security; a critical perspective in the world post Executive Order 14028 (the Executive Order on Improving the Nation’s Cybersecurity). Core to your success in passing the CSA CCZT is understanding that this useful exam is a test of CSA’s proprietary angle on Zero Trust implementations and not general Zero Trust knowledge. I won’t venture an opinion on if CSA’s take is accurate or not, that’s for you to decide. That said, one can gain some foundational comprehension of Zero Trust core objectives through preparing for and taking the CCZT, chiefly that Zero Trust touches all areas of security by ensuring no implicit trust, requiring verification from anyone, and continually validating the identity and access of users and devices, ultimately aiming to minimize security risks in a dynamic and perimeter-less environment. If you keep that in mind, and spend a little time preparing, you can logic your way to a lot of CSA CCZT answers, and come away with a valuable new cert, and potentially some new contextual awareness.
- Disclaimer, I took the CCZT, and wrote this blog, before CSA released the final training module for this certification: Zero Trust Strategy, which focuses on tactics and principles needed to drive Zero Trust objectives, organizational buy-in, and operations; a big value add IMO for all of us looking to answer the inevitable question: “But why should we do this?”
Mack Wartenberger is a mid-level Security Architect with Aquia. If you’ve got more questions about the CCZT or Zero Trust in general, reach out at LinkedIn and if you’re thinking about implementing Zero Trust in your organization let Aquia’s expertise in all things Zero Trust guide you in creating and fortifying your organization’s Zero Trust maturity and overall cybersecurity posture.
If you have any questions, or would like to discuss this topic in more detail, feel free to contact us and we would be happy to schedule some time to chat about how Aquia can help you and your organization.

