A Guide to FedRAMP Levels and DoD Impact Levels for CSPs
Understanding the FedRAMP Authorization & DoD Impact Levels, and how they align
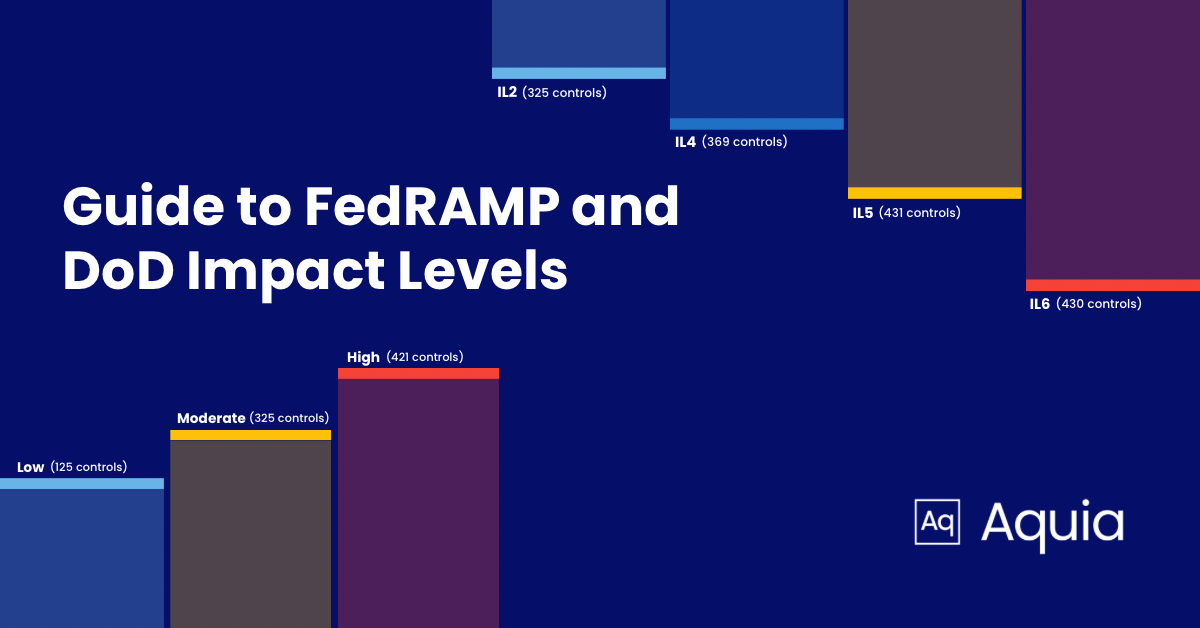
In managing government and military data security compliance standards play an important role in reducing risk. Two important security standards that guide this process are the Federal Risk and Authorization Management Program (FedRAMP) and Department of Defense (DoD) Impact Levels (ILs). It is important that cloud service providers (CSPs) understand these frameworks and explore the distinct levels within each. This post will discuss the significance and implications of each standard and their levels.
Both compliance standards focus on three similar objectives: ensuring confidentiality, integrity, and availability of data.
- Confidentiality: Ensuring safeguards for personal privacy and proprietary information, aiming to prevent unauthorized access or disclosure of sensitive data.
- Integrity: Shielding against the destruction or unauthorized modification of stored information, seeking to maintain the accuracy and trustworthiness of data.
- Availability: Facilitating timely and reliable access to information, emphasizing minimizing downtime and ensuring uninterrupted availability of services.
Understanding FedRAMP Levels
FedRAMP classifies cloud service offerings (CSOs) into three tiers based on the potential impact of a data breach, aligning with the Federal Information Processing Standard (FIPS) 199 standards established by the National Institute of Standards and Technology (NIST).
The three distinct FedRAMP security baseline levels serve as risk indicators for each category. Each level comes with a predefined set of security controls, outlined to meet the specific security needs of that tier. These controls are specific system requirements which contribute to the overall resilience of cloud service offerings, aligning with the goal of safeguarding sensitive information.
-
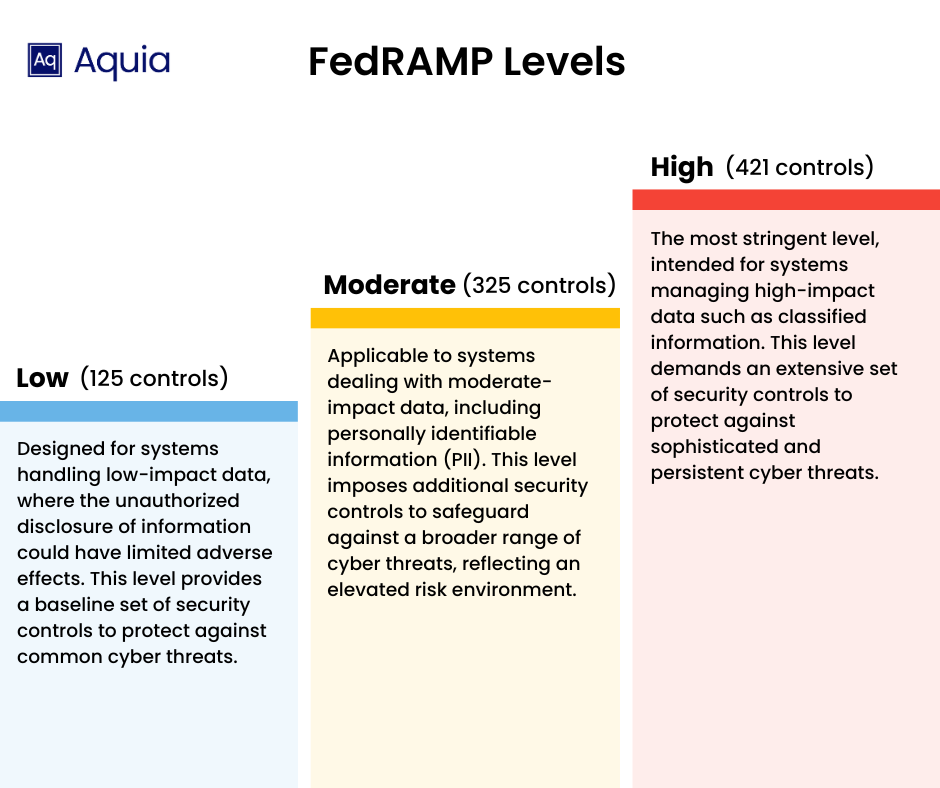
FedRAMP Low (125 controls) FedRAMP Low is designed for systems handling low-impact data, where the unauthorized disclosure of information could have limited adverse effects. This level provides a baseline set of security controls to protect against common cyber threats.
-
FedRAMP Moderate (325 controls) FedRAMP Moderate is applicable to systems dealing with moderate-impact data, including personally identifiable information (PII). This level imposes additional security controls to safeguard against a broader range of cyber threats, reflecting an elevated risk environment.
-
FedRAMP High (421 controls) FedRAMP High is the most stringent level, intended for systems managing high-impact data such as classified information. This level demands an extensive set of security controls to protect against sophisticated and persistent cyber threats.
Understanding DoD Impact Levels
The DoD utilizes Impact Levels, ranging from IL2 to IL6, to classify information systems and the data they manage, taking into consideration potential consequences in the event of a compromise.
In alignment with the guidance provided by the Federal Information Systems Management Act (FISMA) and the NIST Special Publication (SP) 800-37, the Defense Information Systems Agency (DISA) has issued the DoD Cloud Computing Security Requirements Guide (CC SRG). This guide incorporates a FedRAMP+ approach, leveraging reciprocity to adopt security measures established during the FedRAMP process allowing the DoD to utilize a CSO that has been FedRAMP authorized for non-critical mission information and public data. The DoD CC SRG then supplements this foundation with specific requirements and security controls tailored to meet the unique needs of the Department of Defense for sensitive and mission critical workloads.
-
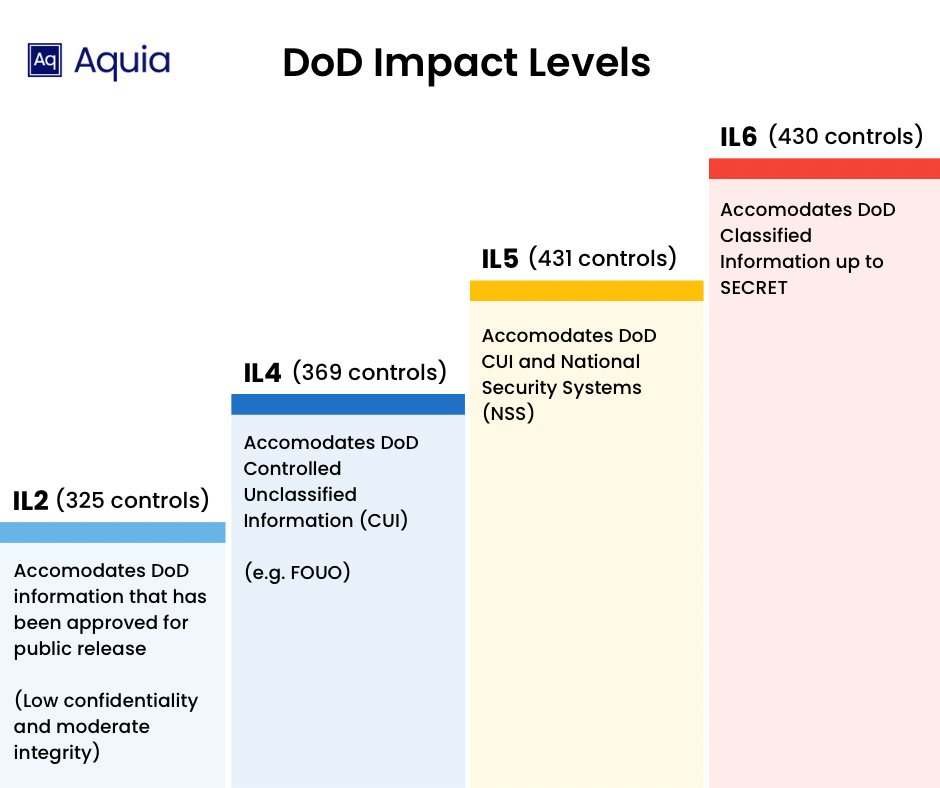
DoD IL2 (325 Controls): Pertains to systems handling Controlled Unclassified Information (CUI), including Public or Non-Critical Mission Information. This encompasses safeguarding information that, while not classified, demands heightened protection to ensure confidentiality and integrity.
-
DoD IL4 (369 Controls): Encompasses a broader spectrum of information, including Controlled Unclassified Information (CUI) such as For Official Use Only (FOUO), Personally Identifiable Information (PII), and Personal Health Information (PHI). Additionally, this level covers Non-Critical Mission Information and Non-National Security Systems (Non-NSS).
-
DoD IL 5 (431 Controls): Includes higher sensitivity CUI, Mission Critical Information, and NSS. Notably, IL5 distinguishes itself from IL4 by explicitly incorporating National Security Systems (NSS) into its scope.
-
DoD IL6 (430 Controls): Encompasses information systems and information classified at the SECRET level. This level is reserved for the most sensitive data, necessitating stringent measures to ensure the utmost confidentiality and integrity.
The Intersection of FedRAMP and DoD ILs
The overlap between FedRAMP levels and DoD ILs is an important consideration for organizations operating in both federal and defense sectors, as it necessitates a comprehensive approach to information security that meets the stringent requirements of both frameworks.
In accordance with Section 5.1.1 of the DoD CC SRG, the CSOs holding a FedRAMP High provisional authorization (PA) are deemed equivalent to a DoD IL4 PA. This recognition streamlines the process for cloud services meeting FedRAMP High standards, allowing the DoD to grant IL4 authorization without the need for additional control assessments. However, it is essential to note that adherence to the non-control and control enhancement (C/CE) requirements outlined in the SRG is imperative. This ensures a comprehensive evaluation, guaranteeing that all IL4 security needs are met.
While FedRAMP Moderate aligns with DoD IL2, and FedRAMP High encompasses 521 of the NIST’s 800-53 security and privacy controls and sub controls, DoD IL 4 and 5 introduce additional layers of security to cater to the unique requirements of the Department of Defense. Specifically, IL5 imposes 11 additional requirements from NIST 800-53 beyond FedRAMP High, along with 18 distinct DoD general requirements. This framework ensures a tailored security approach, acknowledging the distinct nature of information handling within the defense sector.
FedRAMP and DoD IL frameworks align in the following five key areas:
-
Security Controls: Both FedRAMP and DoD ILs emphasize the implementation of robust security controls to safeguard sensitive information. While the specific controls may vary between the two frameworks, the goal remains consistent—ensuring the confidentiality, integrity, and availability of data. Organizations seeking compliance with both standards must adopt a comprehensive set of controls that addresses the unique security needs of both federal agencies and the Department of Defense.
-
Data Classification: The overlap extends to the classification of data. FedRAMP’s Low, Moderate, and High impact levels correlate with the sensitivity of information, while DoD ILs 2 through 6 similarly align with the classification of unclassified to national security systems. This alignment simplifies the process for organizations working with both federal agencies and the military, streamlining data categorization and security implementation.
-
Risk Management and Continuous Monitoring: Both frameworks emphasize a risk-based approach to security. Organizations are required to conduct risk assessments and implement continuous monitoring practices to identify and mitigate potential threats. This shared focus reflects the nature of cybersecurity, where ongoing vigilance and adaptability are critical components of a robust security posture.
-
Interoperability: Organizations operating within the intersection of FedRAMP and DoD ILs often need to address interoperability challenges. Ensuring that security solutions and protocols are compatible with both sets of requirements is crucial. This may involve customizing security measures to meet the demands of each framework while maintaining overall coherence in the security architecture.
-
Vendor and Third-Party Assessments: Vendors and third-party service providers seeking to serve both federal and defense entities must undergo assessments for compliance with both FedRAMP and DoD ILs. This dual validation assures government agencies and military departments that the service providers adhere to the highest standards of security and can be trusted with sensitive information.
Comprehending the nuances of FedRAMP and DoD ILs is vital for CSPs navigating the government and defense sectors. These compliance frameworks help to ensure that systems are not only secure but also aligned with the specific needs and risk tolerances of government agencies and military operations.
If you are interested in learning more or scheduling a consultation to discuss pursuing your FedRAMP authorization, contact us. Backed by a former FedRAMP Joint Authorization Board (JAB) technical representative member, our team understands the nuances, expectations, and critical success factors that can make all the difference when it comes to achieving authorization and scaling within the federal government and DoD.
Looking to learn more about accelerating your FedRAMP journey and expanding your presence within the federal government and DoD? Check out recordings from our Aquia + AWS 2024 Cloud Compliance Summit, a one-day event focused on FedRAMP.
If you have any questions, or would like to discuss this topic in more detail, feel free to contact us and we would be happy to schedule some time to chat about how Aquia can help you and your organization.

